Encrypting Text in a Configuration File
This section details how to encrypt passwords, access keys or other sensitive information in a configuration file managed through Crafter Studio.
The encryption algorithm used is PBE (Password Based Encryption) with AES, in which a password and a salt are specified to generate the key used on encryption/decryption.
Crafter Studio uses a default key and salt for the encryption tool. To set the key and salt to desired values, in your Authoring installation directory, open /bin/crafter-setenv.sh and modify the following values
# -------------------- Encryption variables --------------------
export CRAFTER_ENCRYPTION_KEY=${CRAFTER_ENCRYPTION_KEY:="default_encrytption_key"}
export CRAFTER_ENCRYPTION_SALT=${CRAFTER_ENCRYPTION_SALT:="default_encrytption_salt"}
The encrypted properties work in the following site configuration files:
Engine Site Configuration (
/config/engine/site-config.xml)Studio AWS Profiles (
/config/studio/aws/aws.xml)Studio Box Profiles (
/config/studio/box/box.xml)Studio WebDAV Profiles (
/config/studio/webdav/webdav.xml)
How to Encrypt Text in Configuration File
To encrypt passwords, access keys or other sensitive information in a configuration file managed through Crafter Studio:
Open the configuration file that has the text/information that you would like to encrypt
Find the entry you would like to encrypt and add the attribute
encrypted=""Click on the
Encrypt Markedbutton to encrypt textYour sensitive text should now be encrypted and displayed with the attribute
encrypted="true"and you may now save your file
Example
Let’s take a look at an example of encrypting the accessKey and securityKey for the AWS Profiles configuration.
Open the
AWS Profilesconfiguration file by clicking on ->
-> Configuration, then selectAWS Profilesfrom the dropdown boxWe will add an
AWS S3 profile. Notice that theaccessKeyandsecureKeyis in the clear.{REPOSITORY_ROOT}/sites/SITENAME/config/studio/aws/aws.xml1<?xml version="1.0" encoding="UTF-8"?> 2<aws> 3 <s3> 4 <!-- 5 6 AWS S3 Profile 7 8 Additional properties: 9 10 <bucketName/> 11 <pathStyleAccess/> 12 13 bucketName: name of the bucket where files will be uploaded 14 pathStyleAccess: indicates if path style access should be used for all requests (defaults to false) 15 16 --> 17 <profile> 18 <id>s3-default</id> 19 <credentials> 20 <accessKey>YOUR_ACCESS_KEY</accessKey> 21 <secretKey>YOUR_SECRET_KEY</secretKey> 22 </credentials> 23 <region>us-west-1</region> 24 <bucketName>sample-input-bucket</bucketName> 25 <pathStyleAccess>true</pathStyleAccess> 26 </profile> 27 </s3> 28</aws>
We will now mark items to be encrypted by adding the attribute
encrypted="". For our example, we will markaccessKeyandsecretKeyfor encryption.{REPOSITORY_ROOT}/sites/SITENAME/config/studio/aws/aws.xml<accessKey encrypted="">YOUR_ACCESS_KEY</accessKey> <secretKey encrypted="">YOUR_SECRET_KEY</secretKey>
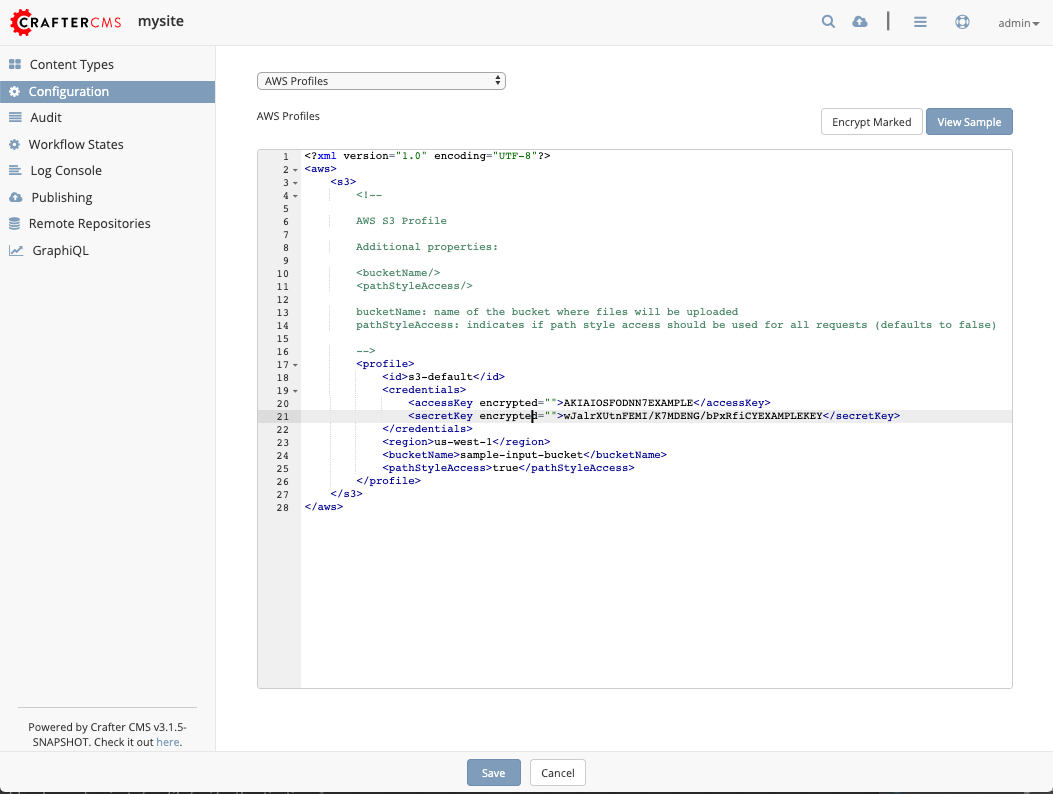
Click on the
Encrypt Markedbutton to encrypt the marked items, the attribute for the marked items will change toencrypted="true":{REPOSITORY_ROOT}/sites/SITENAME/config/studio/aws/aws.xml<accessKey encrypted="true">${enc:ENCRYPTED_ACCESS_KEY}</accessKey> <secretKey encrypted="true">${enc:ENCRYPTED_SECRET_KEY}</secretKey>
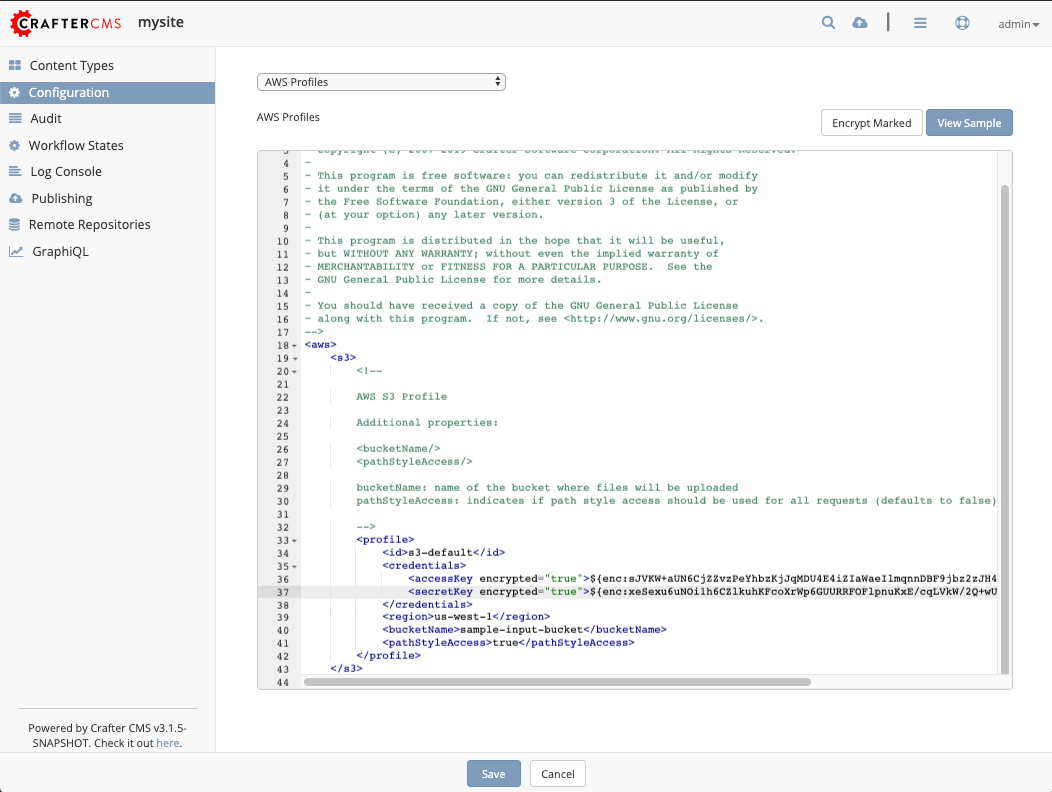
The
accessKeyandsecureKeyis now encrypted and will be decrypted by Crafter Studio as needed