Engine Project Security Guide
The following guide will help you configure Crafter Engine to:
Add authentication for your project.
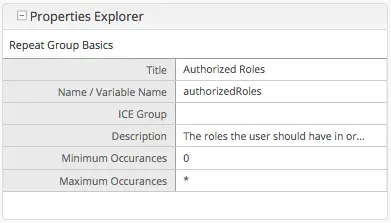
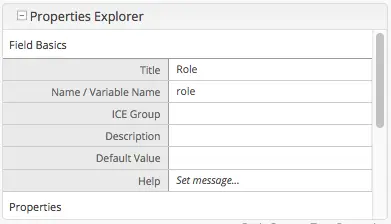
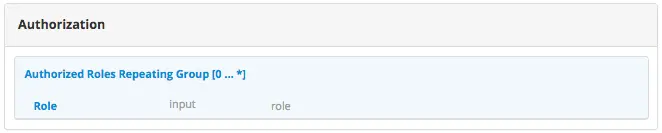
Add authorization so that access to certain pages and URLs of your project are restricted.
Add Authentication
Crafter Engine is able to integrate with multiple authentication providers:
Using SAML2
To configure SAML 2.0, follow the instructions: Engine SAML2 Configuration
Using Crafter Profile
To configure Crafter Profile, follow the instructions: Engine Crafter Profile Configuration then do the following:
Add Login
To add a login page:
In Crafter Studio, create a Home > Login page.
- The page template should contain a form that POSTs to /crafter-security-login, sending the
username, passwordandrememberMeparameters, like in the following snippet:
1<form action="/crafter-security-login" method="post"> 2 <label for="username">Username: </label> 3 <input type="text" name="username"/> 4 <br/> 5 <label for="password">Password: </label> 6 <input type="password" name="password"/> 7 <br/> 8 <input type="checkbox" name="rememberMe" value="true">Remember Me</input> 9 <br/> 10 <button type="submit">Sign in</button> 11</form>
- The page template should contain a form that POSTs to /crafter-security-login, sending the
Add Logout
To add logout, just add a link in the global header that points to /crafter-security-logout:
1<a href="/crafter-security-logout">Log Out</a>
Access User Attributes
Once the authentication and authorization configurations are completed you can use the authToken object in
templates and scripts to access the current user attributes. The class of the object will change depending of the
authentication provider used, but you can always obtain an instance of CustomUser using the principal property.
1<#if authToken??>
2 Hello ${authToken.principal.attributes.firstName}!
3<#else>
4 <#-- show login button -->
5</#if>
Note
You can find more details about the authToken variable in FreeMarker (Templating) API or Groovy API
Migrating from Crafter Profile
Prior to version 3.1.5 Crafter Profile was the only security provider available, all projects created in previous
versions will continue to work without any changes, however if you need to migrate to a different provider like SAML2
you will need to replace all uses of the profile and authentication variables, both have been replaced with
authToken.
In templates and scripts you can replace all uses of profile with authToken and profile.attributes with
authToken.principal.attributes.
Note
Some advanced uses like custom security filters will need to be updated to integrate with Spring Security
Important
The variables
profileandauthenticationwill be null in most cases and should not be used anymore